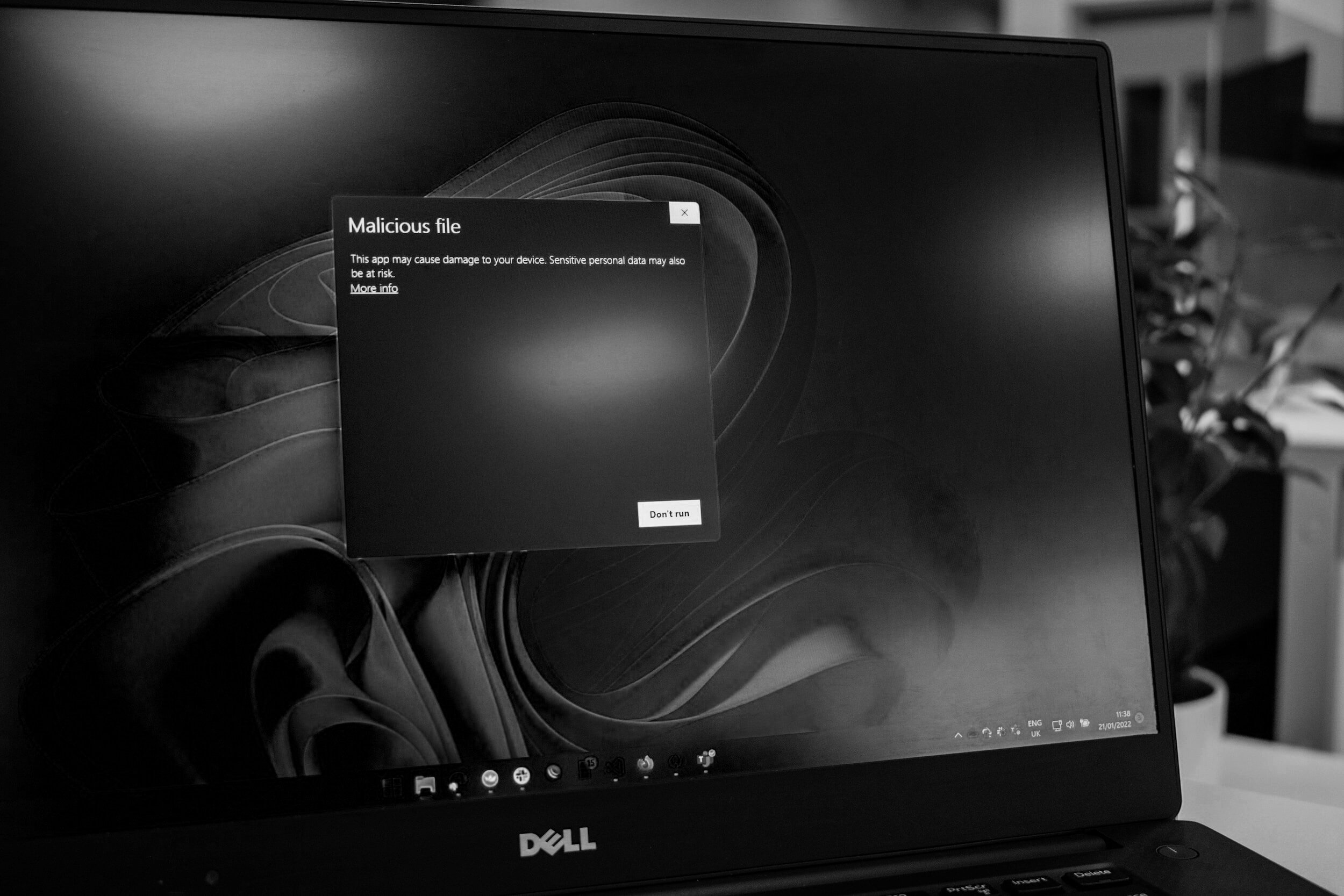
Welcome to Sectreme, your exclusive gateway to bespoke cybersecurity excellence. Unleash the power of tailored protection with our services and elevate your digital defense strategy with precision and expertise.
Why us? Because we take security to the extreme.
-
At the forefront of safeguarding your digital assets, our team leverages advanced technologies and industry best practices to provide comprehensive cybersecurity solutions. Our strategic services focus on proactive risk management, threat intelligence, and tailored security strategies to ensure your organization is prepared for evolving cyber threats. On the policy front, we craft robust frameworks, compliance measures, and governance structures to fortify your defenses. Our commitment extends beyond mere protection; we empower clients with the knowledge and tools to navigate the complex landscape of cybersecurity. Choose us for a holistic approach that not only secures your digital ecosystem but also aligns seamlessly with your organizational goals. With our expertise, rest assured that your digital future is in safe hands.
-
Our comprehensive technical cybersecurity offerings empower clients to fortify their online presence and protect sensitive data. Leveraging state-of-the-art technologies, our expert team provides robust network security, intrusion detection, and advanced threat intelligence services. We specialize in crafting tailored solutions, ensuring a proactive defense strategy that adapts to the dynamic cyber landscape. From robust firewalls to real-time monitoring, our cybersecurity suite is designed to keep your digital assets secure, allowing you to focus on what matters most – your core business. Partner with us to elevate your cybersecurity posture and stay one step ahead in the ever-changing world of online threats. Your peace of mind is our priority.
Our Services

Ready to confront the future?
2024
40%
of all cyberattacks will be linked to session hijacking
30 %
of organizations will experience increased data breaches due to credential theft
55 %
of enterprises will expedite tech consolidation to simplify security
2025
80%
of organizations will fail to protect AI-driven security mechanisms, fueling a vicious cyber risk cycle
60 %
of Fortune 2000 CISO’s will champion transparent, rapid disclosure practices
2026
45%
of Fortune 500 company boards will seek out a chief AI security officer
60 %
of all regulated global entities will struggle to comply with ever-increasing data protection and breach disclosure requirements
Major global powers
will call for a Cybersecurity Geneva Convention
Cybersecurity Predictions for 2024 and Beyond, CyberArk
Want to take security to the extreme?
We understand the importance of protecting your organization from cyber threats. Contact us to learn how our strategic and technical expertise can ensure the security of your digital assets.